Table of Contents
Understanding Tier 0 Assets
In the landscape of IT security, understanding the classification of assets is crucial for effective security posture management. Tier 0 assets refer to the critical infrastructure components that are essential for organizational operations. These typically include domain controllers, identity management services, and other foundational systems that facilitate access to networks and data. The emphasis on Tier 0 cannot be overstated; a breach in these assets can lead to catastrophic consequences, including unauthorized access to sensitive information and the compromise of broader security measures.
The importance of Tier 0 assets extends beyond their immediate function—they serve as the backbone of an organization’s IT environment. Because these assets manage and control user access and permissions across the entire network, they are prime targets for cybercriminals. Thus, ensuring their security becomes a top priority for IT departments. A robust security strategy tailored to protect these assets is necessary to minimize vulnerabilities and strengthen overall IT security.
Retired ESAE – How have we secured in the past?
Source: Microsoft – Enhanced Security Admin Environment
The Enhanced Security Admin Environment (ESAE) architecture (often referred to as red forest, admin forest, or hardened forest) is a legacy approach to provide a secure environment for Windows Server Active Directory (AD) administrator identities.
Microsoft’s recommendation to use this architectural pattern has been replaced by the modern privileged access strategy and rapid modernization plan (RAMP) guidance as the default recommended approach for securing privileged users. This guidance is intended to be inclusive of adapting a broader strategy to move towards a Zero Trust architecture. Given these modernized strategies, the ESAE hardened administrative forest architecture (on-premises or cloud-based) is now considered a custom configuration suitable only for exception cases.
Very high level from an architectural view the design looked like this:

You will still hear about this design from the legacy world and there are also some use cases for “disconnected” environments, but Security and Cloud Architects should look into modernizing this approach.
Certain components and approaches used in the ESAE are still valuable and are now considered “good cyber hygiene” like dedicated Privileged Access Workstations. Like many other components in a security strategy, this is a whole story by itself. Take a look here, if you want to know more.
Can we use Azure Arc for Tier 0 / Privileged Access Devices?
This depends on your use case and your environment. If you are licensed or plan to use modern Cloud Security solutions included in M365 E3 and M365 E5 licenses, Windows Defender for Identity or Entra ID to manage these Privileged Access Devices in a modern way, than you also should consider to Azure Arc enable the devices.
Be aware that Azure Arc does support Windows 11 and Windows Server, so you can get a single contral plane for the configuration of your Domain Controllers and other Tier 0 servers including Linux.
When using Azure Arc you should continue using the seperation from ESAE and maintain minimum privileges.
When utilizing Azure Arc, it is important to uphold the practice of separating from ESAE and ensuring minimal privilege access.
Recommendations when using Azure Arc with Tier 0
Dedicated Azure Subscription
One of the key strategies for enhancing the security of Tier 0 assets is to maintain a dedicated Azure subscription. This approach isolates the critical resources from other less secure environments, significantly reducing the risk of lateral movements by attackers. By securing Tier 0 assets in a dedicated environment, organizations can focus their security measures on these vital components without interference from other cloud services or applications that may have differing levels of security requirements.
Disable Unnecessary Management Features for Azure Arc
Another critical aspect of securing Tier 0 assets is to disable unnecessary management features that may serve as attack vectors. Many cloud environments come with a plethora of features that, while beneficial in certain contexts, may not be necessary for every organization. Features such as public endpoint access, unnecessary administrative privileges, and unused APIs can introduce vulnerabilities. Therefore, it is essential to conduct a thorough assessment of all management features to identify those that are non-essential.
For Azure Arc this is information shared here by Microsoft and i copied it here.
For a Tier 0 asset, you should use the local agent security controls to disable any unused functionality in the agent to prevent any intentional—or accidental—use of those features to make changes to the server. This includes:
- Disabling remote access capabilities
- Setting an extension allowlist for the extensions you intend to use, or disabling the extension manager if you are not using extensions
- Disabling the machine configuration agent if you don’t intend to use machine configuration policies
The following example shows how to lock down the Azure Connected Machine agent for a domain controller that needs to use the Azure Monitor Agent to collect security logs for Microsoft Sentinel and Microsoft Defender for Servers to protect against malware threats:
azcmagent config set incomingconnections.enabled false
azcmagent config set guestconfiguration.enabled false
azcmagent config set extensions.allowlist “Microsoft.Azure.Monitor/AzureMonitorWindowsAgent,Microsoft.Azure.AzureDefenderForServers/MDE.Windows”Secure the Network conncection
When using Azure Arc and other solutions like Windows Defender you will need an internet connection. For Azure Arc this is solved by using the new “Azure Firewall Explicit proxy (preview)” and the configuration for Azure Arc is described here. This article is part of the Azure Arc configuration, but can easily be used with other Azure services. If you need support configuring Azure Arc for a proxy, please check my guide here.
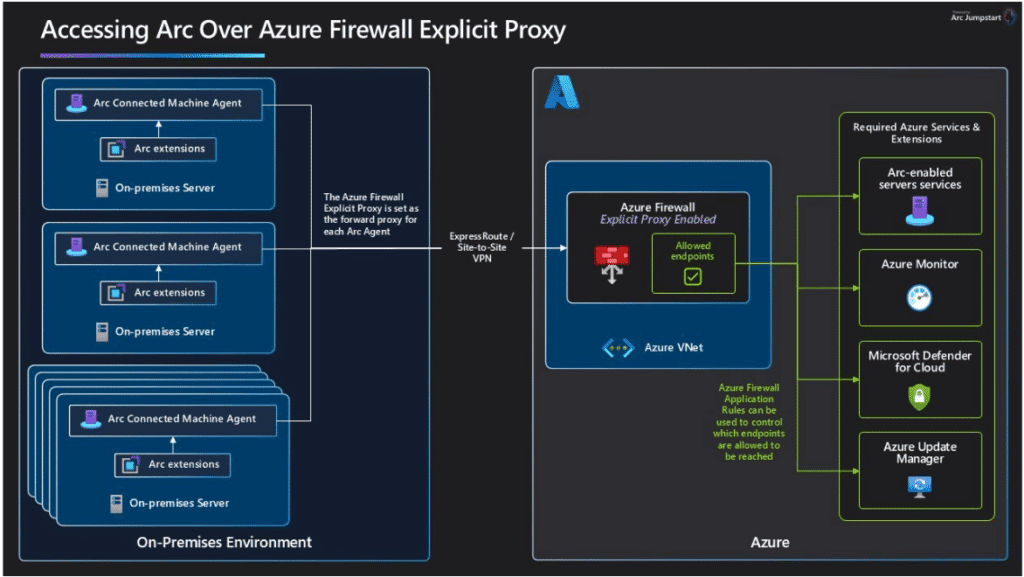
A higher quality image of the image above can be found on the Azure Arc Jumpstart website.
The other option to enable a secure communication with Azure Arc is the Azure Arc Gateway. This solution does help simplifying the connectivity, when you already have Firewall solutions in place like a next gen firewall.
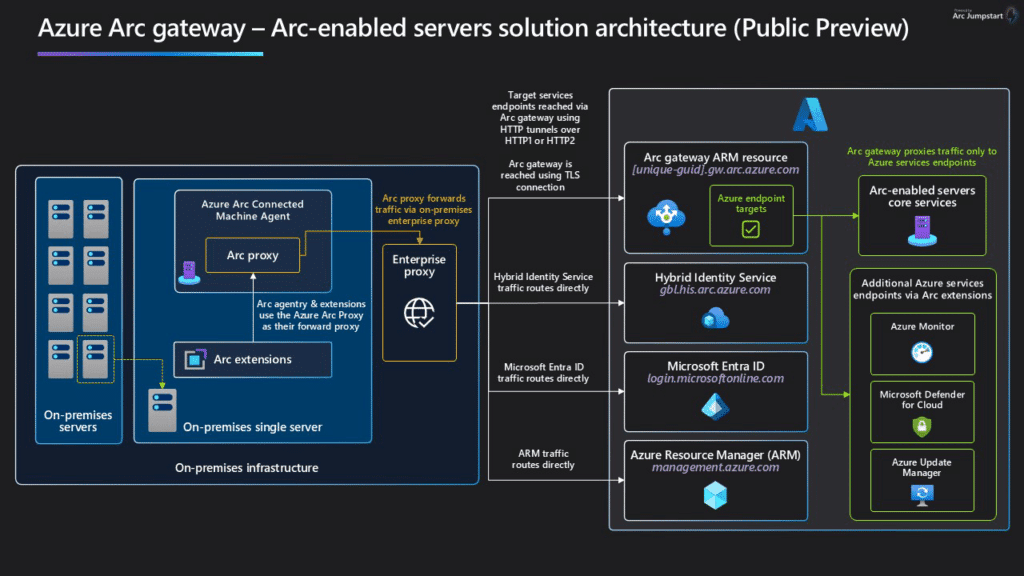
Background on Tier 0 the Modern Way
Evolution of Tier 0 Security
The concept of Tier 0 security has evolved significantly over the years. Initially viewed as a static construct, modern interpretations recognize the dynamic nature of IT environments and the need for adaptive security measures. As organizations move to cloud-based infrastructures, the boundaries of traditional Tier 0 assets have blurred, necessitating a re-evaluation of security approaches. Today, Tier 0 encompasses not just on-premises systems but also cloud-based identity and access management solutions.
Modern Tier 0 security strategies incorporate automation, machine learning, and artificial intelligence. These technologies enhance threat detection and response capabilities, allowing organizations to proactively identify and mitigate risks. Continuous monitoring is integral to these strategies, enabling real-time visibility into the security status of Tier 0 assets and facilitating rapid incident response.
Current Trends and Technologies
Several current trends are shaping the future of Tier 0 security. Zero Trust Architecture is at the forefront, emphasizing the need to authenticate and authorize every access request, regardless of whether the request originates from inside or outside the network. This model is particularly relevant for Tier 0 assets, as it ensures that even trusted users are subject to stringent security checks.
Another significant trend is the shift towards identity-centric security strategies. With the increasing sophistication of cyber threats, organizations are prioritizing identity management as a critical layer of security for Tier 0 assets. Advanced identity protection solutions, such as those powered by AI, are being deployed to detect anomalies and prevent unauthorized access based on behavioral patterns.
Microsoft on ESAE and Tier 0
The Enhanced Security Admin Environment (ESAE) architecture (often referred to as red forest, admin forest, or hardened forest) is a legacy approach to provide a secure environment for Windows Server Active Directory (AD) administrator identities.
Microsoft developed ESAE and accepted that while components of it are still valid, the design needs to evolve into the cloud world with Zero trust and modern technologies.
Microsoft recommends organizations with ESAE/hardened forests adopt a modern privileged access strategy. Use guidance from the rapid modernization plan (RAMP) as this guidance complements existing ESAE implementations.
It provides security for roles not protected by ESAE, such as:
- Microsoft Entra administrators
- Sensitive business users
- Standard enterprise users
For more information, refer to the article on securing privileged access security levels.
Conclusion and FAQs
In summary, securing Tier 0 assets is a multifaceted endeavor that requires a comprehensive understanding of their importance within the IT security landscape. By adopting best practices such as maintaining a dedicated Azure subscription, disabling unnecessary management features, and leveraging modern technologies like Azure Firewall and Azure Arc, organizations can significantly enhance the security of their critical infrastructure. As cyber threats continue to evolve, so too must the strategies employed to protect these vital assets.
What do we want to achieve? Take a look at the below screenshot and get your architects for Endpoint, Security, Active Directory, Entra and Network together to discuss how to start a journey from ESAE to Modern Server Management.

FAQs
What are Tier 0 assets?
Tier 0 assets refer to critical infrastructure components essential for organizational operations, including domain controllers and identity management services. These assets are crucial for managing access and permissions across the network.
Why is it important to secure Tier 0 assets?
Securing Tier 0 assets is essential because a breach can lead to unauthorized access to sensitive information and disrupt core operations, resulting in significant financial and reputational damage. This is often related and caused by a “golden Kerberos ticket” usage event. Check more details about this here.
How can a dedicated Azure subscription enhance security for Tier 0 assets?
A dedicated Azure subscription isolates critical resources, minimizing the risk of lateral movements by attackers and simplifying compliance with data protection regulations.
What is Azure Arc, and how does it help secure resources?
Azure Arc extends Azure management capabilities to on-premises and multi-cloud resources. It allows organizations to implement consistent security policies and gain centralized visibility over Tier 0 assets.
How can disabling unnecessary management features improve security?
Disabling unnecessary management features reduces the attack surface for Tier 0 assets by limiting potential entry points for attackers and minimizing the risk of exploitation.
What are Privileged Access Workstations / devices?
Privileged Access Workstations (PAWs) or devices are specialized systems designed to provide a secure environment for performing sensitive tasks, such as administrative activities and managing critical infrastructure. These devices are part of a comprehensive privileged access strategy and are implemented to ensure the highest level of security for privileged accounts. For more detailed information, you can visit the Microsoft Learn page on Privileged Access Workstations.





