In this article you’ll explore how security, governance and lifecycle risk converge in modern infrastructure, why the recent Microsoft SFI report matters for hybrid-cloud and on-prem environments, and how you can treat trust as an architectural dimension in your stack.
Table of Contents
Introduction to Secure Future Initiative
When infrastructure architects talk about technical debt, we usually mean outdated servers, unsupported firmware, drifted configurations. But there is another dimension that too few pay attention to: trust—and with it, timing.
The Microsoft Corporation November 2025 progress report on its Secure Future Initiative (SFI) draws a line under that idea: security isn’t a feature you bolt on, it’s a foundation you build proactively.
As someone who writes about infrastructure governance, hybrid-cloud architecture and the accrual of operational risk, this hits home: we aren’t just modernising hardware or shifting workloads; we’re reinforcing the trust fabric of our systems.
Why the SFI Progress Report Matters for Hybrid / Infrastructure Teams
At first glance, the report reads like a portfolio of big numbers and enterprise milestones: 95 % of employees trained on AI-powered attack defences, 99.6 % of MFA for Microsoft devices, new governance functions added across regions.
What resonates for us on the hybrid side is how these institutional efforts reflect on infrastructure timing debt:
- The “Secure by Design / Secure by Default / Secure Operations” mantra means your on-prem stack, your edge nodes, your hybrid connectors must keep pace—not slower, but equal-footed.
- Microsoft’s governance scale-up (new Deputy CISOs, European Security Programme, supply-chain oversight) reminds us that hybrid/cloud isn’t simply about technology — it’s about ecosystem readiness and alignment.
- The large engineering-scale statistics underline one thing: trust is a measurable output. The infrastructure that hosts cloud, identity, data must be timely, secure, governed. Delay here is not just cost—it’s risk.
In other words: If you treat your infrastructure upgrade as “nice to have next year,” you are accumulating trust-debt.
My Point of View: Architecture, Timing & Trust
From my vantage point working across on-premises servers, hybrid network stacks, VLANs, Azure Arc connectors, I see three key reflections:
1. Timing is trust acceleration
In the past we accepted servers running 5 years, firmware unsupported, or skipping one upgrade cycle. We said: “It still works.” But in the SFI report the message is clear: systems will be exploited unless upgraded, unless defaults are hardened, unless governance is continuous.
So the architectural lesson: don’t treat upgrade delays as neutral—they’re slow erosion of trust.
2. Hybrid stacks blur the boundary of responsibility
Microsoft’s emphasis on governance, ecosystem supply chain and global readiness means that your on-prem, your edge, your hybrid link to cloud are no longer separate islands. If identity, network or firmware lag, your hybrid application spans become risk vectors.
As someone who writes about technical debt in infrastructure, the parallel is clear: just like code debt compounds, governance debt and trust debt compound across environments.
3. Security and architecture are not optional extras
When I discuss infrastructure with clients and in the blog, I often point to “lifecycle planning”, “upgrade waves”, “modernisation budgets”. The SFI report reinforces: security must be embedded from inception through operations—not bolted on after.
In practice this means: adopt secure-by-default configurations, plan for identity hardening, enforce patch cadence, and visualise your “trust architecture” alongside your network/compute diagram.
What You Should Do Now about Secure Future Initiative in your environment
Given these perspectives, here are my actionable suggestions for hybrid-cloud/infrastructure teams:
- Audit your trust surface. Identify all “entry points” in your environment: identity, network, edge, cloud connectors. Ask: are they on supported versions? Do they meet secure-by-default baselines?
- Map your upgrade backlog as trust-debt. Every delayed migration = interest paid in risk and integration cost. Tag those items in your backlog as “trust-debt” and prioritise accordingly.
- Align governance with architecture. Ensure your architecture review board includes governance/third-party/supply-chain oversight. Document roles, responsibilities, accountability (echoing Microsoft’s Deputy-CISO model).
- Adopt secure defaults across your hybrid stack. Use baseline frameworks (e.g., NIST, Zero Trust) and make sure your on-prem, edge and cloud components conform. The SFI report explicitly provides patterns and practices.
- Communicate the timestamp. In architecture documentation, include “valid-as-of” dates for firmware, OS versions, connector versions. Make clear when the next wave is scheduled. Let the clock be visible.
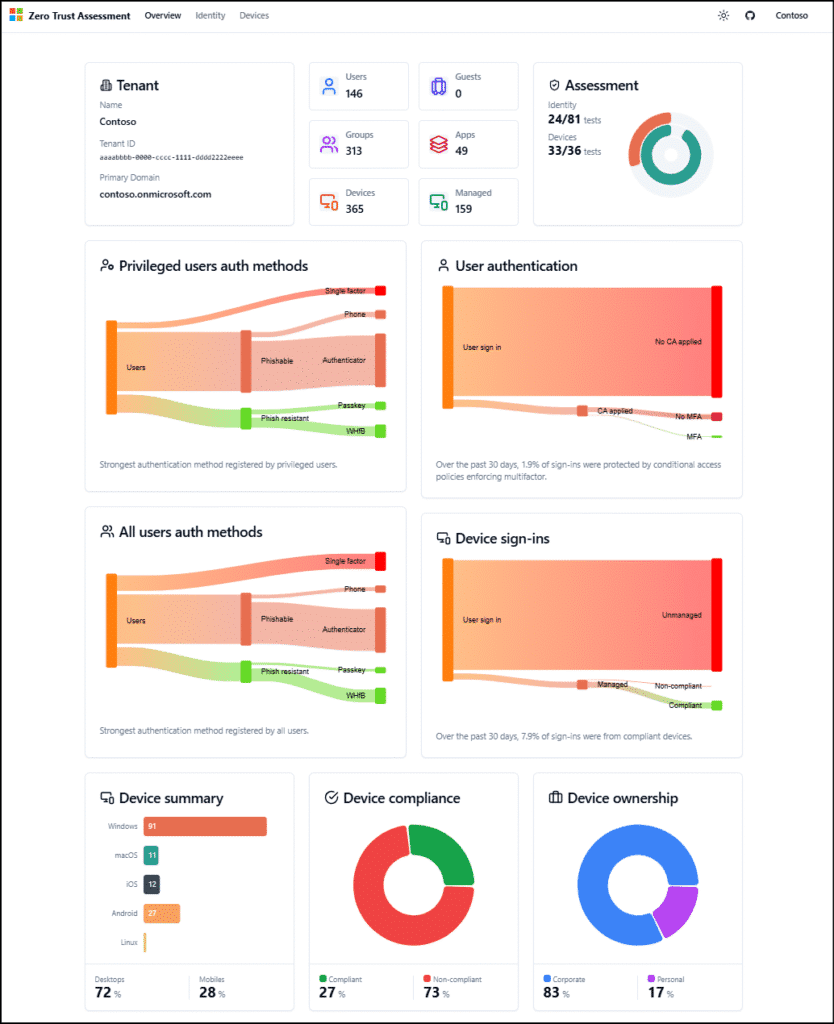
Start with the Zero Trust Assessment today to operationalize Zero Trust principles.
Conclusion
Security is no longer a secondary concern—it is foundational. The Secure Future Initiative November 2025 report from Microsoft underscores that modern infrastructure must be timely, governed, resilient, and trustworthy.
If your upgrade cycle drags on, if your edge nodes are unsupported, or if your hybrid connectors are stale, you aren’t just behind—you are eroding trust.
For infrastructure architects, hybrid teams and governance leads, the call is clear: modernise your timing, reinforce your trust architecture, treat security as architecture.
Because in our interconnected, multi-cloud, edge-infused world, your architecture isn’t just code—it’s commitment.
If you are interested in this area, I do recommend reading my content on technical debt “Overcome Technical Debt in IT Infrastructure 2025” and my guide on Windows Server 2025 – Part 7 (Active Directory Hardening)
If you have any questions please don’t hesitate to reach out to me on LinkedIn, Bluesky or check my newly created Adaptive Cloud community on Reddit.
LinkedIn: https://www.linkedin.com/in/andreas-hartig/
Bluesky: https://bsky.app/profile/hartiga.de
Adaptive Cloud community on Reddit: https://www.reddit.com/r/AdaptiveCloud/
Sources:
Securing our future: November 2025 progress report on Microsoft’s Secure Future Initiative
November 2025 SFI Progress Report
Explore actionable patterns and practices from the Secure Future Initiative (SFI)