Automation using Group Policy is most likely the easiest step in your environment for custimzation. In one of the latest Blog articles we looked into “Group Policies and Group Policies Preferences” and now we want to use that foundational knowledge, to get a few GPOs deployed.
This will be an ongoing series of GPO / GPP tipps and tricks and this will show the background to learn about the basics, file shares used and give you a certain guidance. The GPOs will be created while I automate, optimize, customize and secure my homelab.
Table of Contents
Where to store scripts, wallpapers & assets for Group Policies
When storing assets for GPO deployment, consider the trade-offs between using SYSVOL and a dedicated file share.
Personally I never use the sysvol of a Domain Controller. Even if there are scripts recommending it to be used in their default settings, i.e. Azure Arc onboarding, I will re-create the scripts and always use a fileshare on a distributed file share. In the homelab I will use my non DFS enabled fileserver and create a folder with read rights for everyone.
Important Keep anything > 50 MB out of SYSVOL. Group Policies client downloads are synchronous; a 4 K wallpaper or software deployment on a Wide Area Network or Client VPN will ruin your morning coffee.
| Location | Pros | Cons |
|---|---|---|
\\domain\SYSVOL\…\Scripts | Replicates automatically; no extra share needed | DFSR can choke on ISO images; pollutes backups |
Dedicated file share (e.g. \\infra\gpoassets$) | Clean separation; quota-controlled; easier RBAC | Must replicate manually (RoboCopy/DFS-R); extra ACLs |
I created a Fileserver for my homelab and for the GPO related files, I will use a simple approach.
- Attach an additional disk “GPOs” to your Fileserver
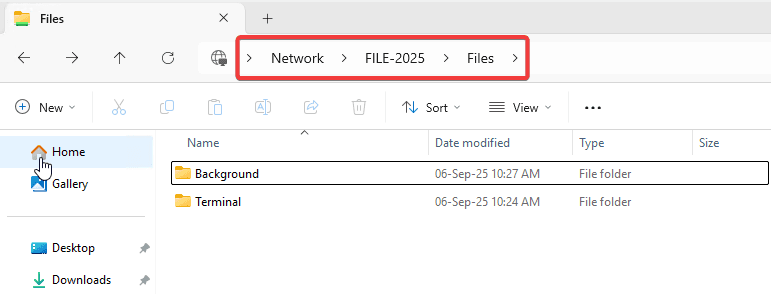
- Create a folder structure /Files/Background, /Files/Terminal/,…
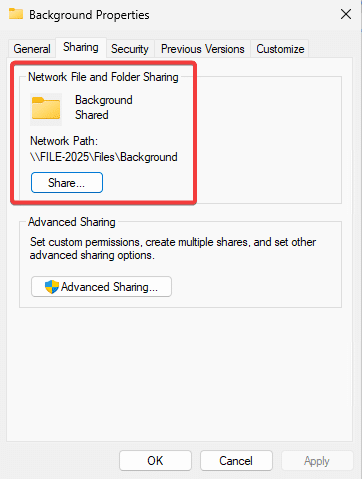
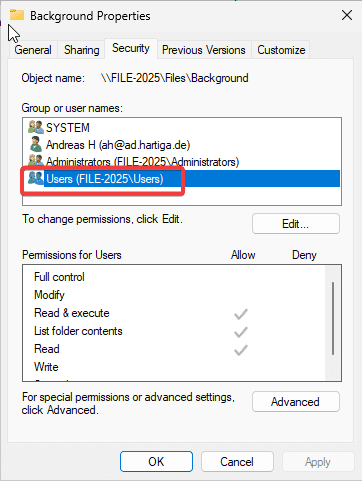
- Share the Folder Files to Users with Read Access Only
- Verify access rights to users are configured as per default
What is our goal here for Automation using Group Policy?
Whenever we deploy a new server in our homelab, we do have to automate certain tasks. In my homelab it is the customization of Background, Windows Terminal, the installation of Software using Winget and implementing Auto Updates for software like Azure Arc.
This can get annoying and boring, but also will create issues with keeping things up to date and work reliably. After being over 1.5 years into this blog, i most likely have used hours for repetitive tasks. While initially this is good to learn the basics, we want to also get to the next level.
Naming convention for GPOs
Use short, predictable parts to achieve Automation using Group Policy. Example pattern:
<ENV>-<Side>-<Area>-<Purpose>-<Scope>
- ENV =
LAB,DEV,PROD - Side =
C(Computer) orU(User) — this is about processing side, not link location - Area = broad bucket like
UX,AppMgmt,Security,Network,Browsers - Purpose = one intent, e.g.
Wallpaper,WingetAutoUpdate,LocalAdmins - Scope = optional—
Workstations,Servers,Kiosk,VDI,All
Keep versions/owners out of the name. Put those in the GPO Comment (Purpose, Owner, Change/Issue, Version/Date, Link to runbook).
As you can see by the naming convention, this will create a simple rule set by itself.
- One intent per GPO. Don’t make kitchen-sink GPOs. Easier rollback and auditing.
- Don’t mix sides. Keep User and Computer settings in different GPOs.
- Split by target. Separate Workstations vs Servers vs Special roles (Kiosk/VDI).
- Split by volatility. Things you tweak often (UX) shouldn’t live with slow-moving baselines (security).
- Prefer OU linking over heavy security filtering. Use security groups sparingly for exceptions.
- Use WMI filters carefully (e.g., only Clients). Over-filtering = slow processing, harder troubleshooting.
- Document in the GPO comment. Purpose, owner, change log, and any special pre-reqs.
My recommendations
Keep Automation using Group Policy simple. You can fix a lot of things using GPOs, but that doesn’t mean you should. I have seen very complex GPOs to assign printers, default printers, configure applications, map dozen of network shares and systems running a dozenz scripts.
- Link location: Link where the objects live (Users OU for user policies; Computers OU for computer policies).
- Security Filtering: Default to
Authenticated Users(Read + Apply). Use a “GPO_<Thing>_Allow` group only for true exceptions. - Item-level targeting (GPP): Use to refine file copies or tasks (e.g., only laptops, only if file missing). GPP are your friend. Learn how to use them to replace scripts using Item Level Targeting (copy files, map drives,…)
- Central Store: Keep ADMX in a Central Store so every DC reads the same templates.
- Comments: Fill the GPO comment (owner, purpose, version/date, link to your runbook/readme).
- Testing: Staging OU with a few test objects, then roll out.
- Ordering: Don’t encode numbers in names; order is controlled per link.
- For Security exceptions create tickets and map them to GPOs using the ticket number with the exception. Request security approval for each of the assignments.
- grpresult is your best friend
- Policy Analyzer is your second best friend.
1. Background Pictures
Why Background Pictures?
I want customized background pictures for multiple reasons:
- Identify Servers that are fully managed
- Identify my Domain Controllers visually
- Utilize customized backgrounds to show it is my “personal content”
- Create a feeling of “standardization”, “customized” and a “good take care of environment”
Don’t underestimate giving environments a personal or corporate branding. People will notice that there is a team / IT organization taking care of this. In very large scale environments this might not work, but your personal environments or smaller business settings will benefit from this.
Naming convention and details
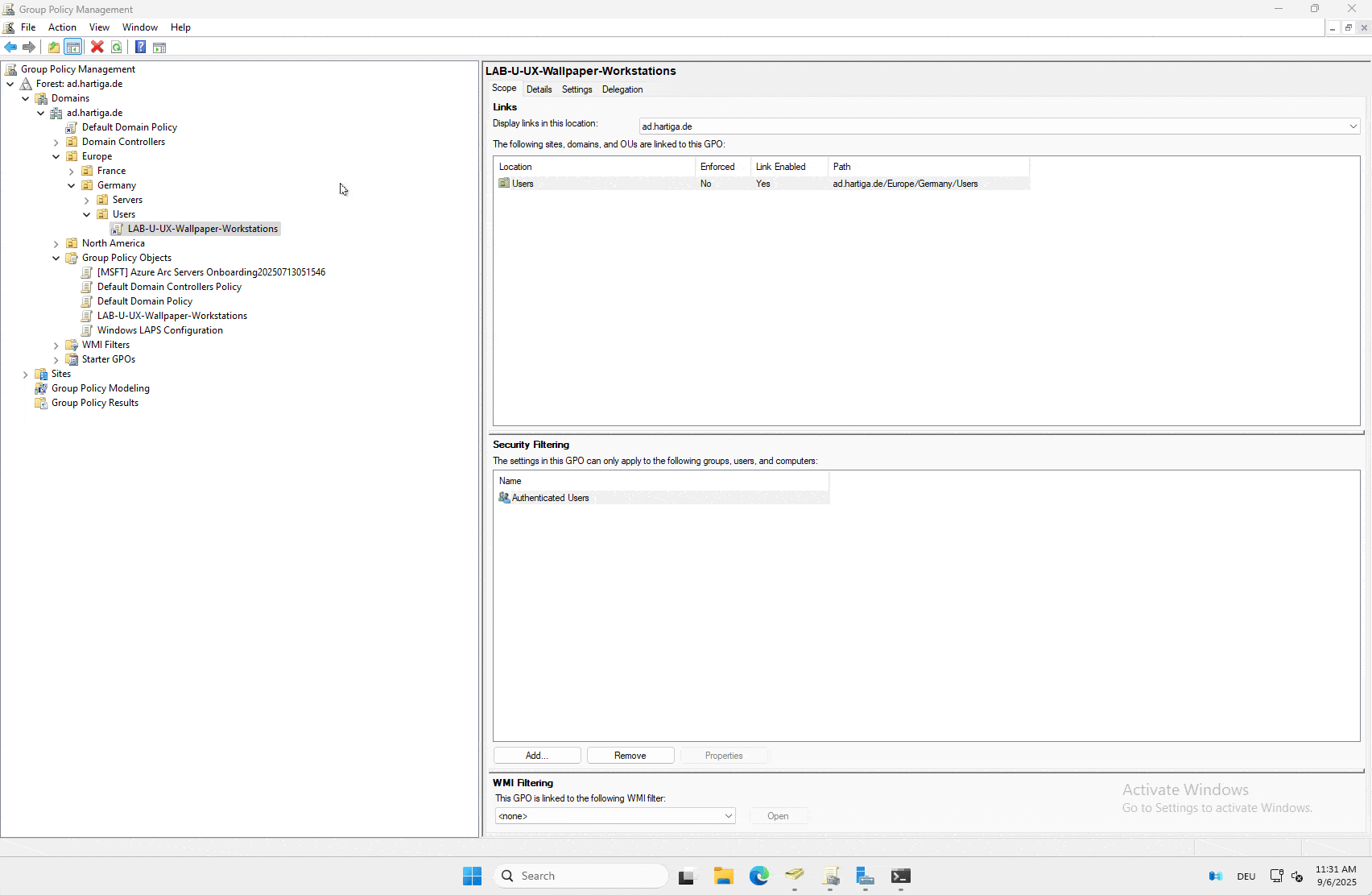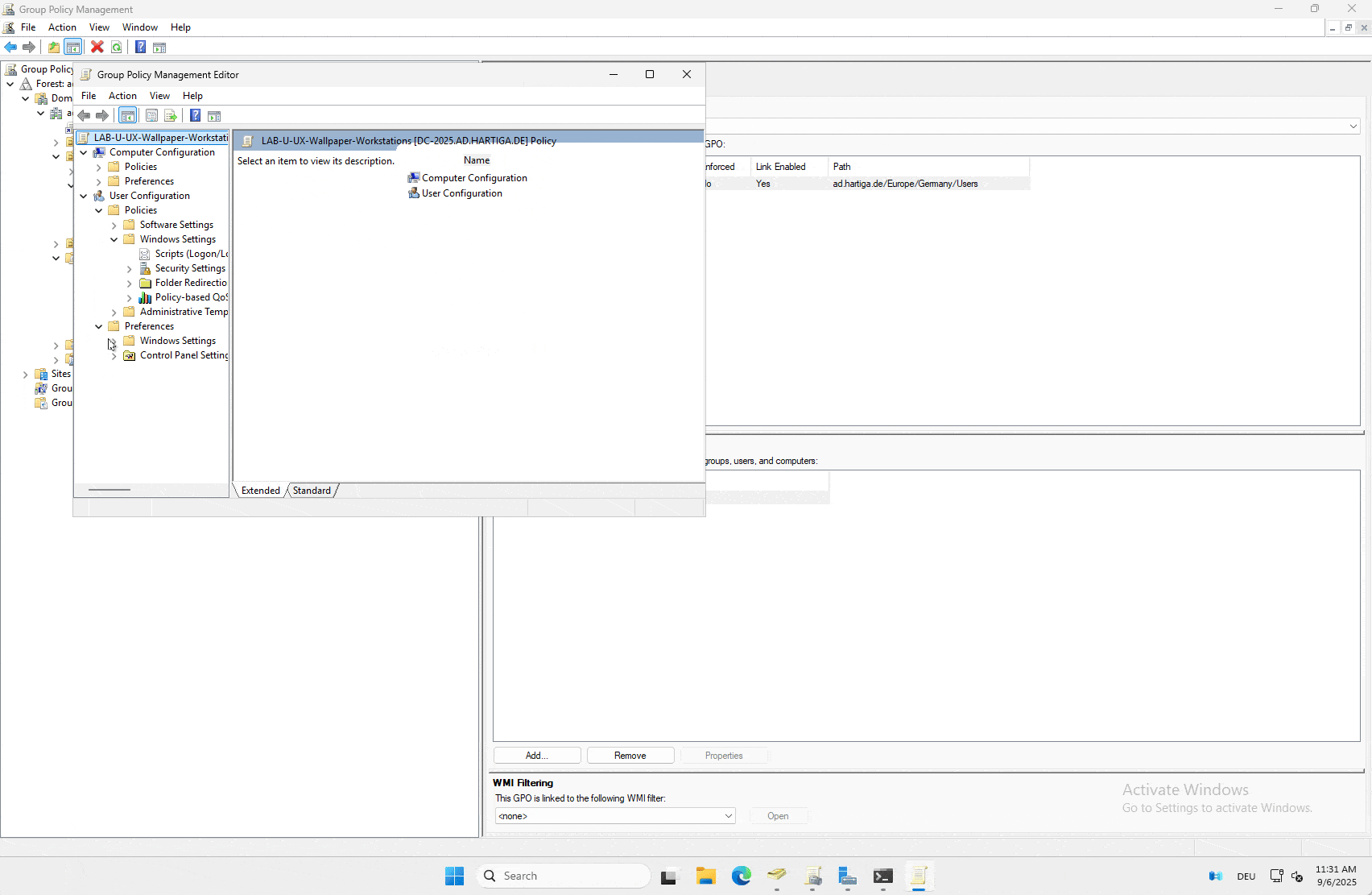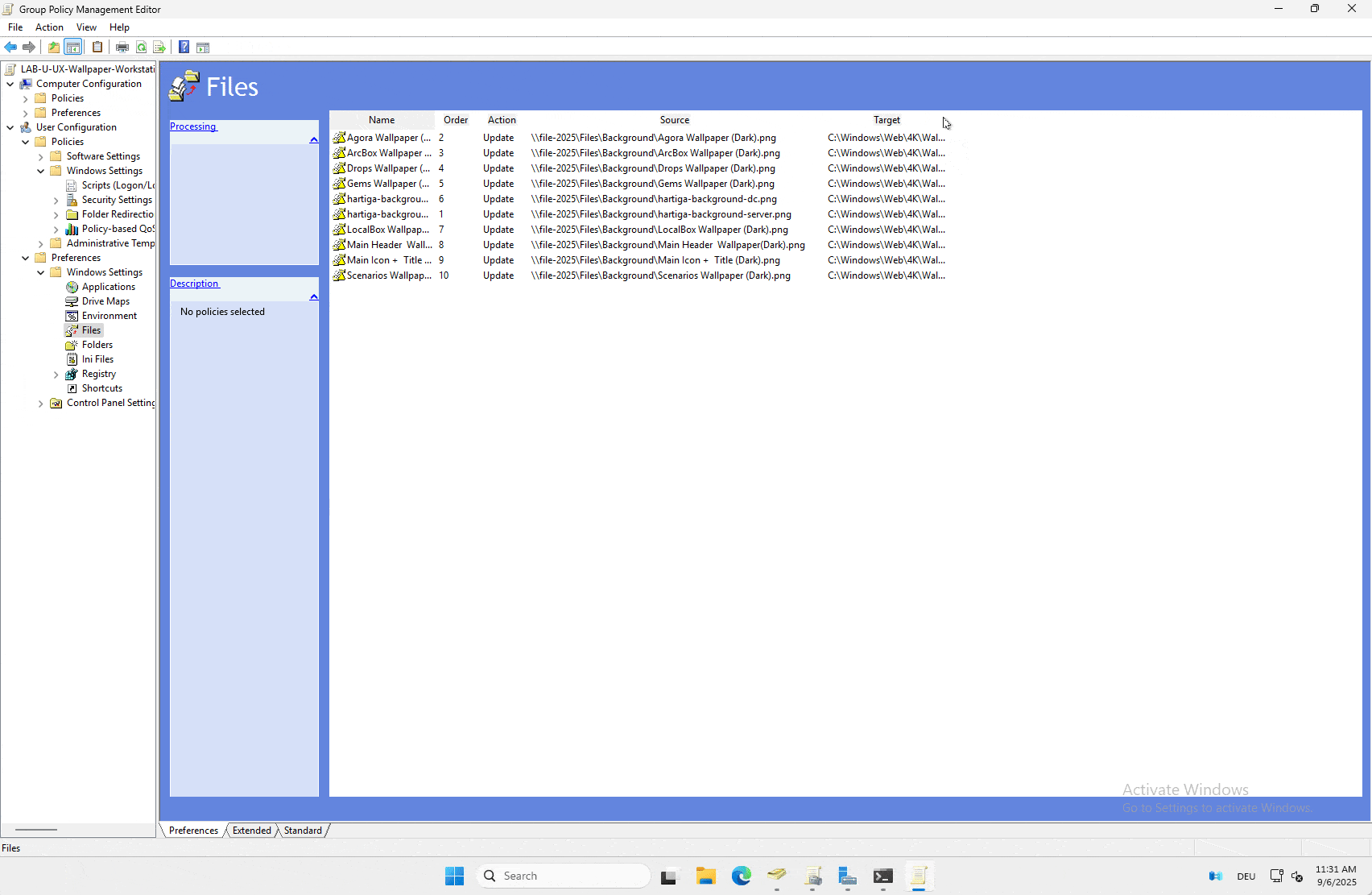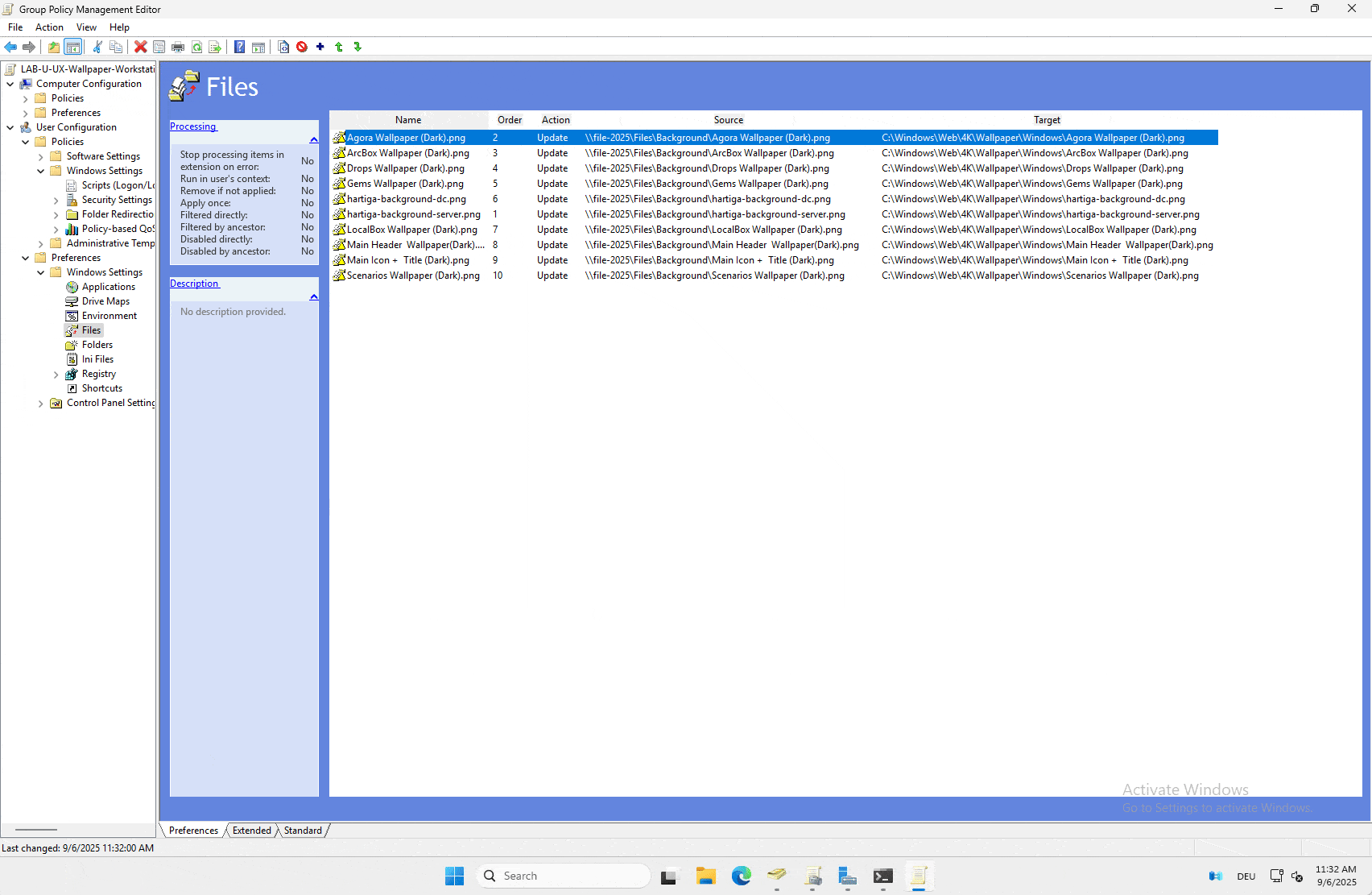
Name: LAB-U-UX-Wallpaper-Workstations
Link to: OU containing the users who should get the wallpaper.
Important: Do not try to make your Automation using Group Policy Windows background perfect with a Marketing team. You might be surprised how many resolutions you have in the organization and how complex getting “perfect” pictures for each resolution will be. Keep the size ~ 2-4 MB per file and copy them using GPP to reduce the risk of performance issues.
Microsoft Link: Configure the desktop and lock screen backgrounds
Other guides: Step by Step using Screenshots
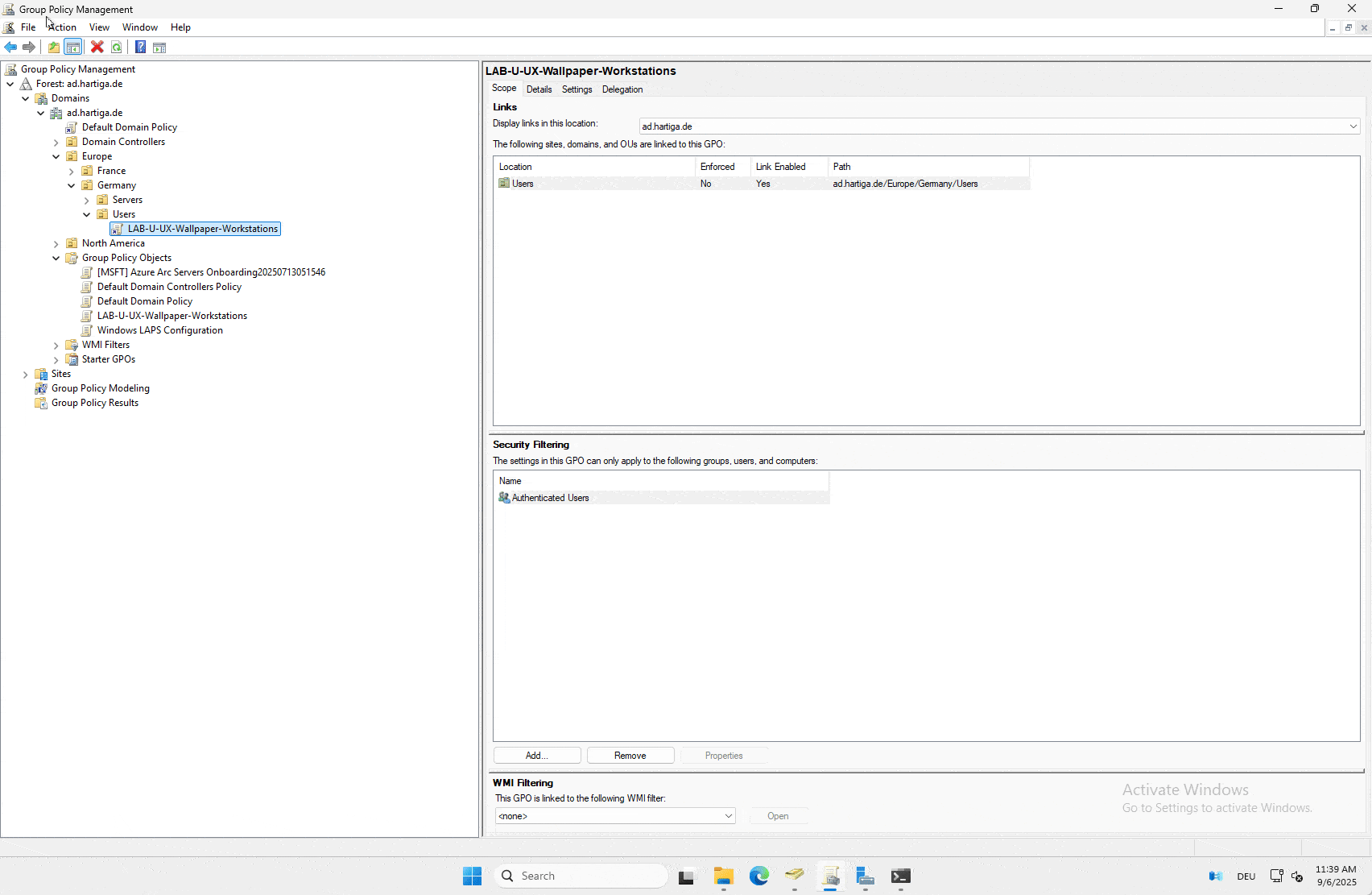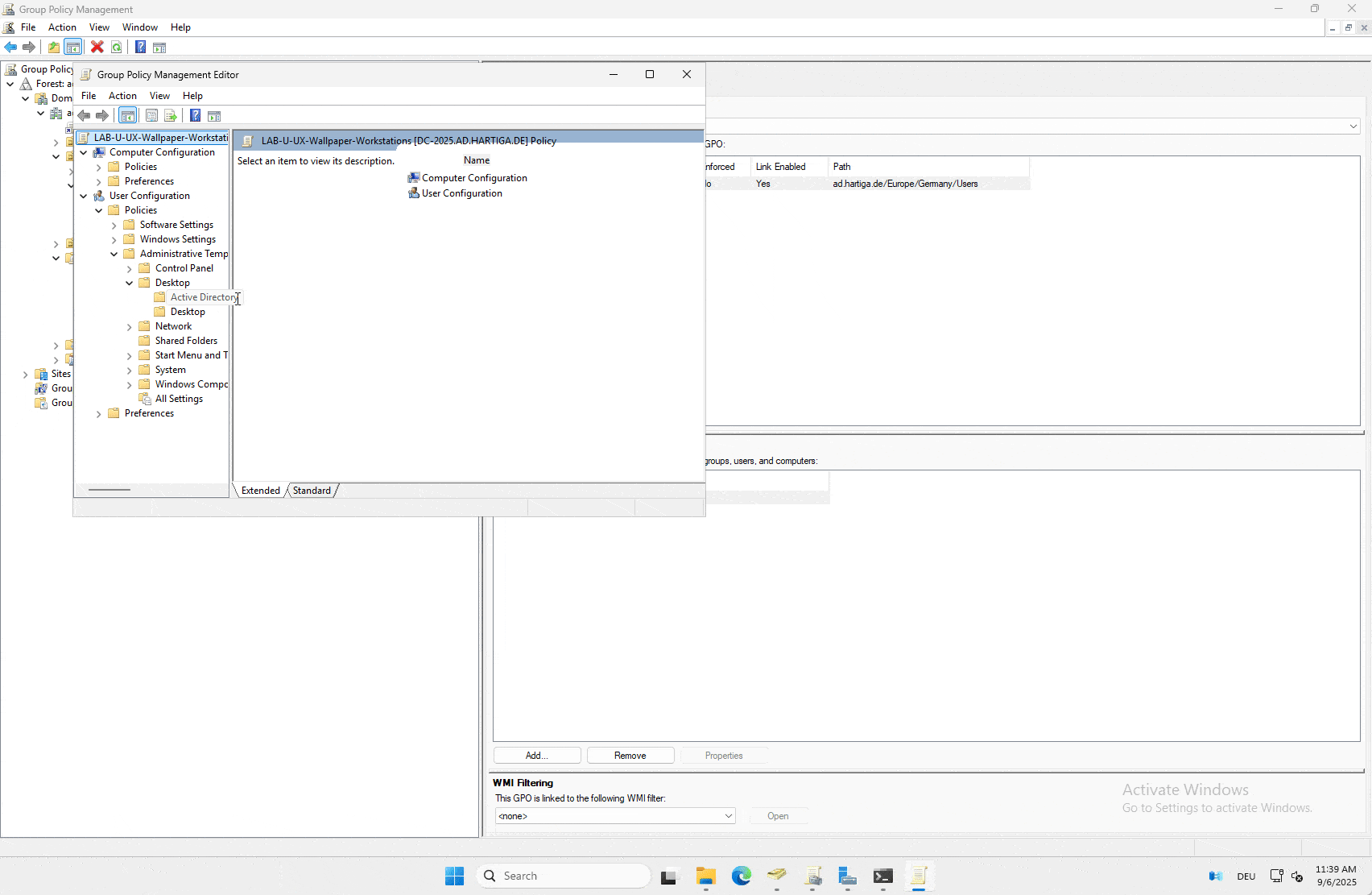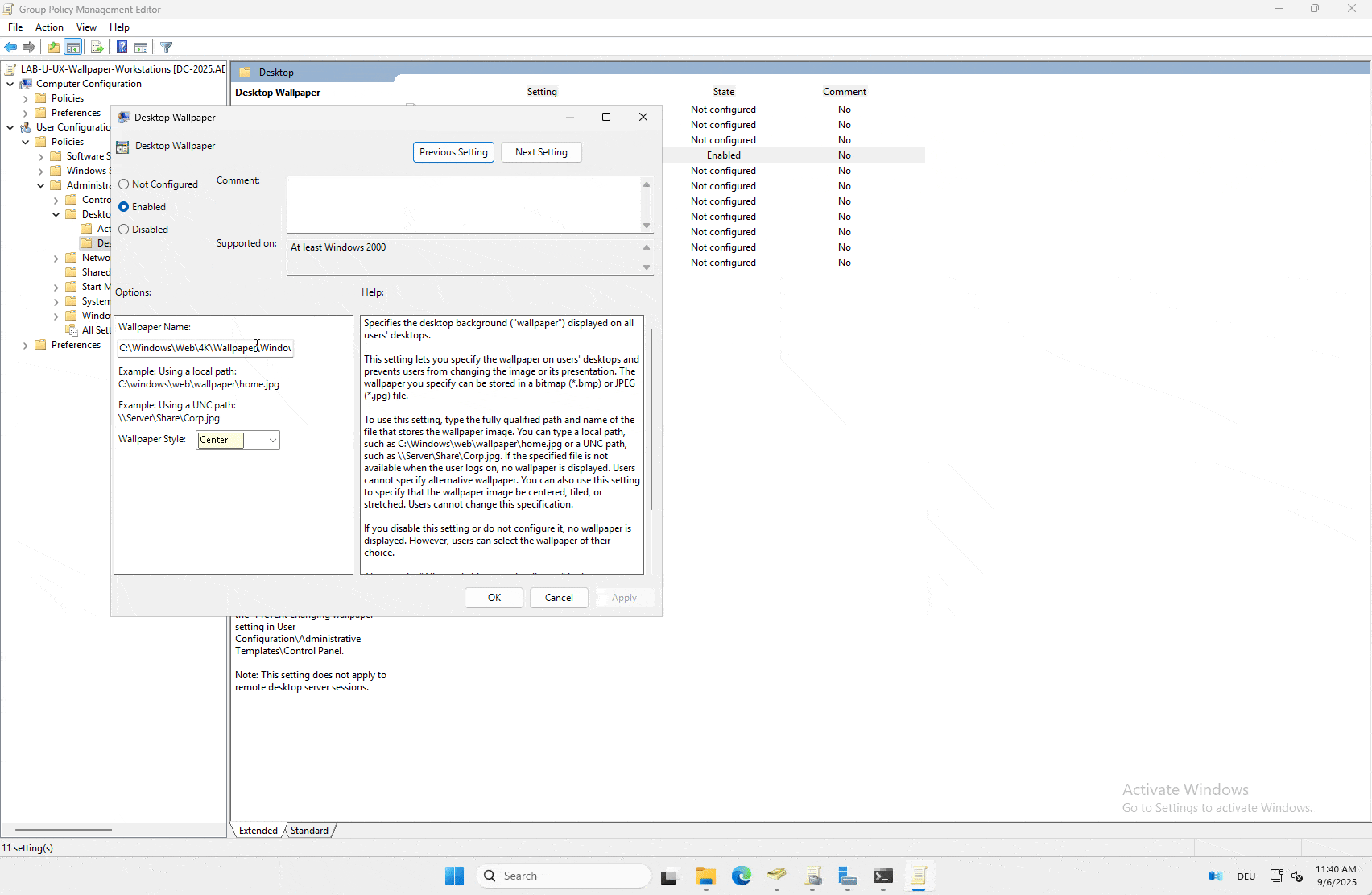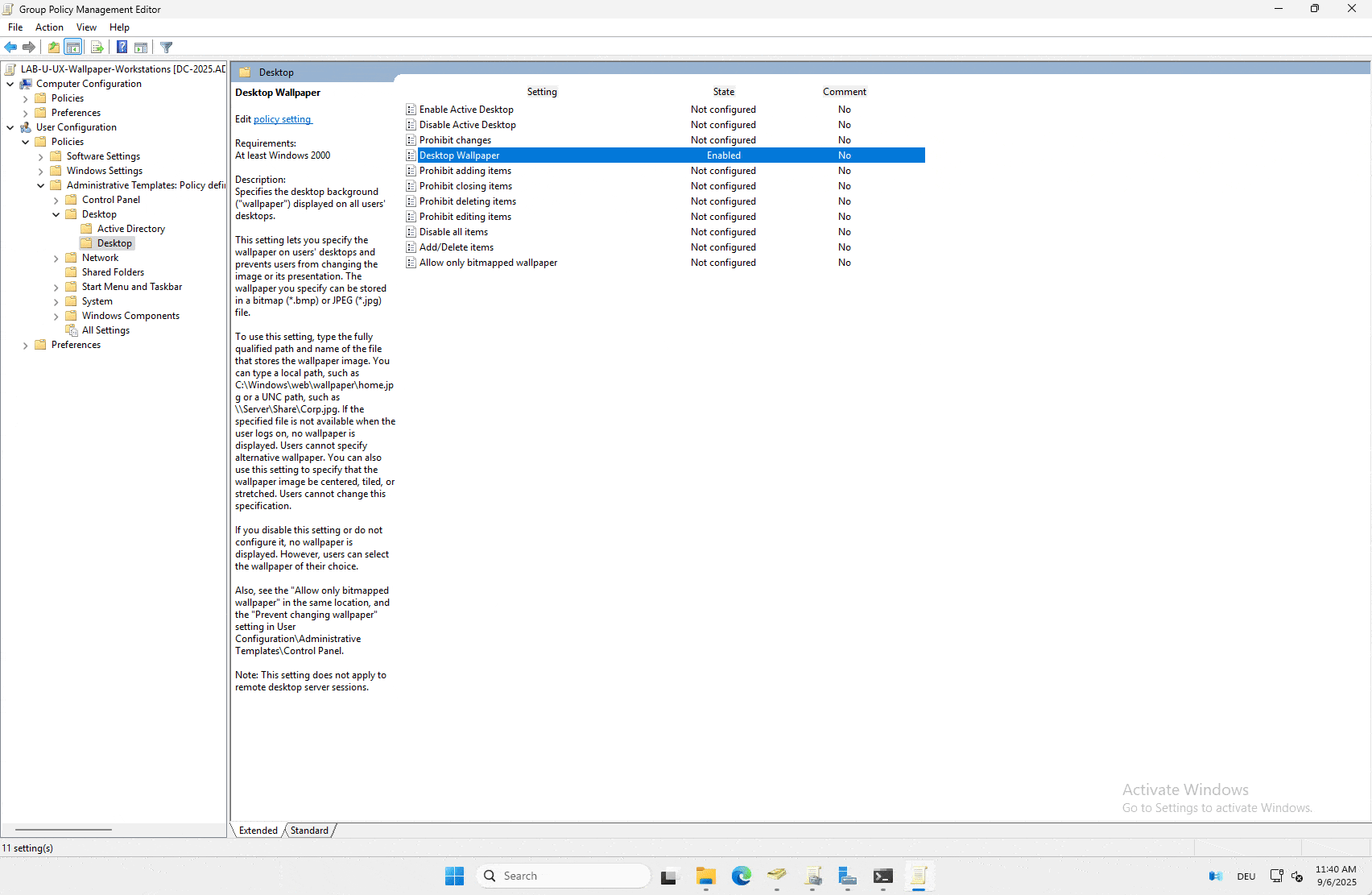
My learnings: The GPOs and most guides are not updated. You can use *.png files these days as your background option.
GPP – File Copy
We will be copying the file from \file-2025\Files\Background to C:\Windows\Web\4K\Wallpaper\Windows\ using the GPP component. To learn more about GPP please check the foundation article here.
GPO – Configuration
We will use this new GPO to configure all our servers to use the hartiga-background-server.png file. For this GPO it is important to know, that you have to logoff / logon again. You can only use the gpresult to verify that the GPP has copied the file.
Conclusion
I wanted to share 5 – 10 GPOs in this article and noticed, that there is a lot of basic work and understanding needed. Even for the most simple and standard GPO for an updated wallpaper, there are many steps involved. For these guides I have decided to split them into multiple stories and use animated GIFs to visualize the steps needed.
GPOs can grow very complex in environments. I have seen IT projects running for years to standardize thousands of GPOs, when the person “owning” GPOs left the company. Documentation, Standardization and “keeping it simple” are your business friend. This includes not building very nested GPO structures or trying to fix everything with a GPO.
If you are building your first GPOs and design the environment, I would highly recommend to involve a consultant with experience in this area. One day of training and guidance will easily save you plenty of time doing cleanup and troubleshooting later.
If you have any questions please don’t hesitate to reach out to me on LinkedIn, Bluesky or check my newly created Adaptive Cloud community on Reddit.





