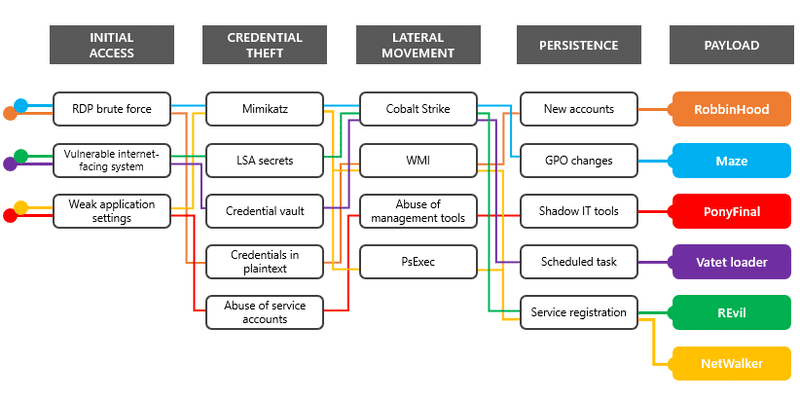
In today’s world, cybersecurity is not just a necessity; it’s a foundation for your business’s integrity and trustworthiness. One of the key components of this foundation is Active Directory hardening. Think of Active Directory as the backbone of your network’s security. Without rigorous protection, it’s vulnerable to attacks that could compromise your entire system.
Understanding and implementing AD hardening measures can be complex and technical. To help you navigate this journey, I recommend starting with an informative series of blog entries from the Microsoft Core Infrastructure and Security Blog written by Jerry Devore that break down some high priority tasks including step-by-step guides to get them implemented.
Table of Contents
Chapter 1: Disabling NTLMv1
Active Directory Hardening Series – Part 1 – Disabling NTLMv1
Summary: NTLMv1 is an outdated authentication protocol that poses significant security risks. This blog article explains why and how to disable NTLMv1 to enhance your AD’s security. By removing this weak link, you make it harder for attackers to compromise credentials.
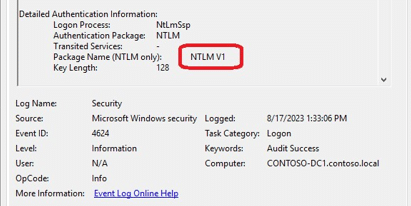
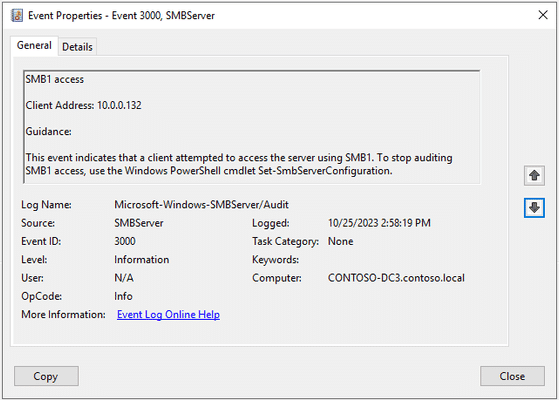
Chapter 2: Removing SMBv1
Active Directory Hardening Series – Part 2 – Removing SMBv1
Summary: Similar to NTLMv1, SMBv1 is an outdated protocol with known vulnerabilities. This blog article guides you through the process of removing SMBv1 from your network, ensuring that your file sharing and network communications are more secure.
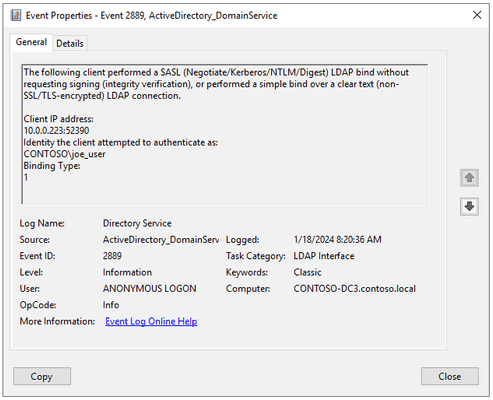
Chapter 3: Enforcing LDAP Signing
Active Directory Hardening Series – Part 3 – Enforcing LDAP Signing
Summary: LDAP signing improves the security of LDAP communications, preventing man-in-the-middle attacks. This blog article explains the importance of enforcing LDAP signing and provides a detailed walkthrough on how to implement this critical security measure.
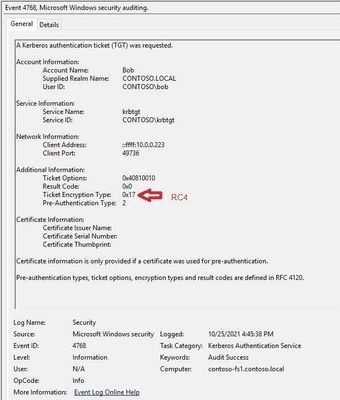
Chapter 4: Enforcing AES for Kerberos
Active Directory Hardening Series – Part 4 – Enforcing AES for Kerberos
Summary: Kerberos is a key protocol for secure authentication within AD. By enforcing AES encryption for Kerberos, you significantly enhance the security of your authentication processes. This blog article article offers insights into the benefits of AES and how to configure it in your environment.
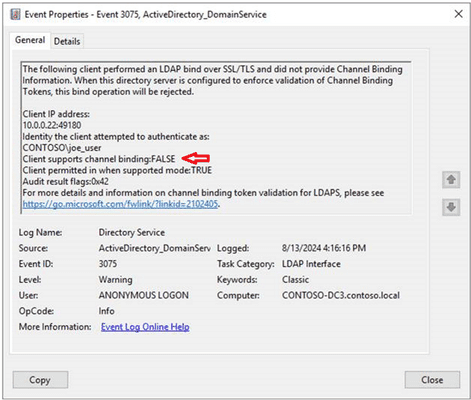
Chapter 5: Enforcing LDAP Channel Binding
Active Directory Hardening Series – Part 5 – Enforcing LDAP Channel Binding
Summary: LDAP channel binding is another essential security feature that ensures the integrity and confidentiality of LDAP communications. This blog article discusses why channel binding is necessary and provides step-by-step instructions on how to enforce it in your AD setup.
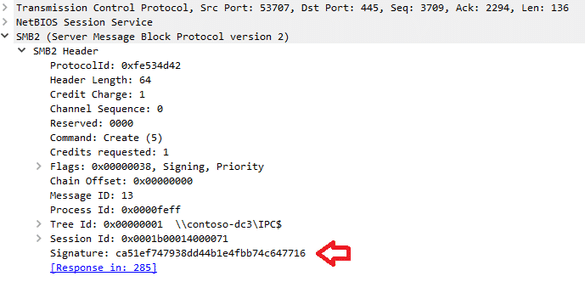
Chapter 6: Enforcing SMB Signing
Active Directory Hardening Series – Part 6 – Enforcing SMB Signing
Summary: SMB signing protects the integrity and authenticity of SMB traffic, preventing tampering and spoofing attacks. This blog article explains the benefits of SMB signing and demonstrates how to enable it, ensuring your file transfers are secure.
Chapter 7: Implementing Least Privilege
Active Directory Hardening Series – Part 7 – Implementing Least Privilege
Summary: The principle of least privilege is fundamental to minimizing security risks. By ensuring that users have only the access necessary for their roles, you reduce the potential damage from compromised accounts. This blog article provides practical advice on how to implement and maintain least privilege in your AD environment.
Chapter 8: Reporting
In case you want to check on how well you implemented some of these hardening components and more, please check the Microsoft AD As Built Report by Jonathan Colon on Github.
Check their example report on their Github Repository. It does come with AD Site and Services reports, unlinked GPOs and an unlimited number of other information.
Conclusion
By following these blog articles, you’ll gain a thorough understanding of AD hardening and be well-equipped to secure your network against potential threats. Remember, cybersecurity is an ongoing process, and continuous learning and adaptation are key to staying ahead of attackers. Stay vigilant and proactive in protecting your digital assets!
Check my blog article on how to get started with Windows LAPS and follow me on bluesky and LinkedIn for daily updates.





