Windows Server 2025 Autologon is a challenging discussion. Learn why, when and how to enable Autologon in Windows Server 2025 safely, plus robust mitigation strategies.
A reboot that lands on the Ctrl-Alt-Del screen is a fatal faux-pas in any self-respecting homelab. When you run headless nodes in a rack at 2 a.m., tip-toeing past sleeping family or barking dogs, Auto Login on Windows Server 2025 feels like that extra cup of coffee you forgot you needed – until you realise the security tab you just tore off the tin can.
This article will not encourage you to use Autologon. It will teach you the basics and risks, so you know why this is not a recommendation in your productive environment. If you have to use it, at least understand the best practices and risks.
Table of Contents
Why Autologon?
Convenience is the obvious lure, but in a homelab context it is often automation that tips the scale. Scheduled tasks, DSC pulls, or your nightly Winget update job all might count on reaching a PowerShell prompt post-reboot without human intervention.
You might want to run something for your family, i.e. a Steam based Satisfactory, Minecraft or Palword Game Server and notice, that stability does require reboots and you want to automate things in a way, that your family can handle.
AutoLogin is a quick and dirty fix in homelab to automate a script or run something in a predictable way.
Why Not Auto Autologon? What Are the Risks
Every upside hides a trapdoor. Autologon will store your password in a readable format in HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon in plain-text by default; anyone with physical access – or VHD/VMDK access – can scoop it up in seconds. The same applies when you use the Sysinternals Autologon utility: although the tool encrypts the string, it merely swaps one registry location for another, still recoverable with enough patience and a memory debugger. Check the technical details here, if you want to learn about the LSA encryption and read here why it is not secure.
On domain-joined machines the blast radius is even wider. The account often enjoys Domain Users (and sometimes Domain Admins), turning a lab curiosity into a privilege-escalation trampoline. Kerberos tickets issued after AutoLogin will happily be cached; lateral movement is only one script away.
Microsoft’s own article formerly known as KB324737 warns that “The autologon feature is provided as a convenience. However, this feature may be a security risk.”
Important: AutoLogin reduces the interactive logon barrier but widens the attack surface dramatically. Think physical security and credential hygiene and every other alternative, before using this.
Use Registry Editor to Turn On Automatic Logon
Those who have never used this method and are in operational IT roles over 10 years can throw the first rock. Here is your powershell script to enable autologon using a user created manually and logged in for testing.
Username: AutoLogin
Password: You_should_not_do_this!
# Run as Administrator
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon' `
-Name AutoAdminLogon -Value '1' -Type String
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon' `
-Name DefaultUserName -Value 'AutoLogin'
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon' `
-Name DefaultPassword -Value 'You_should_not_do_this!'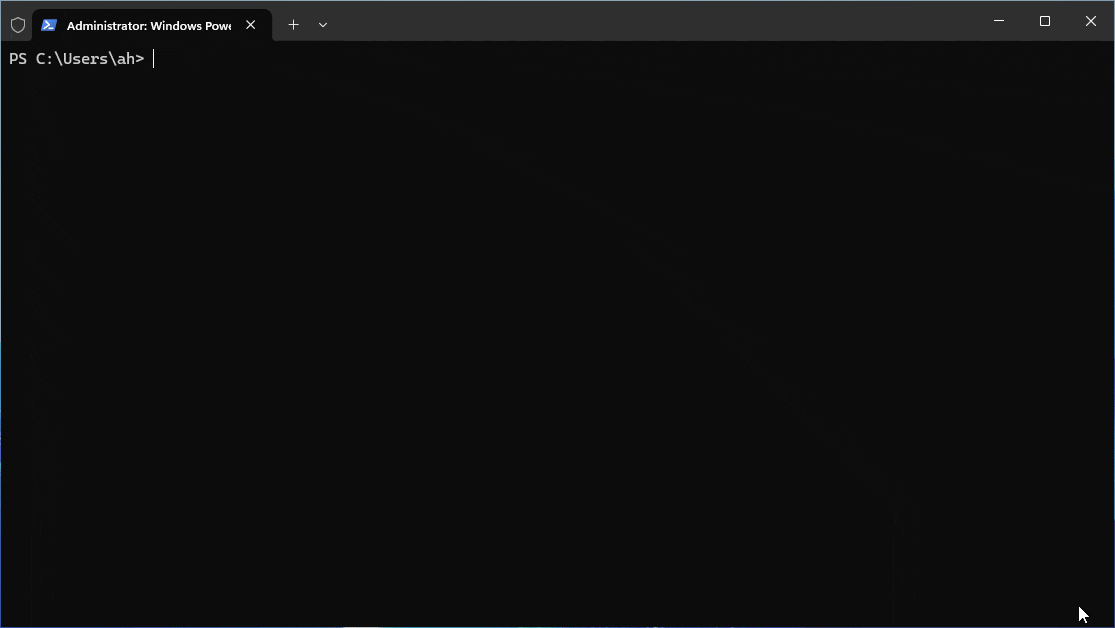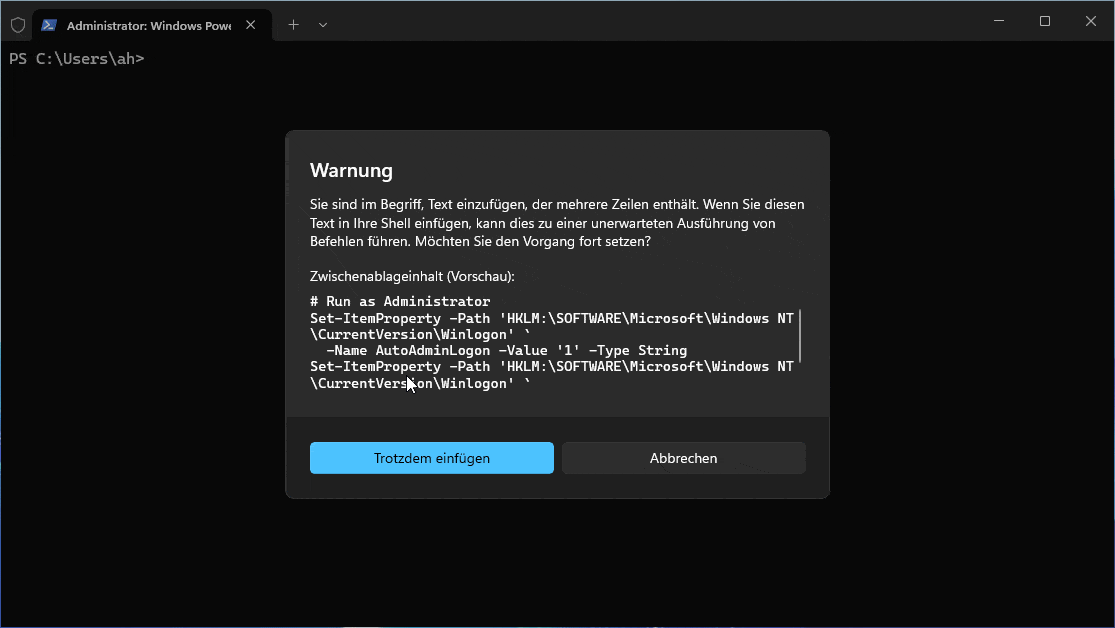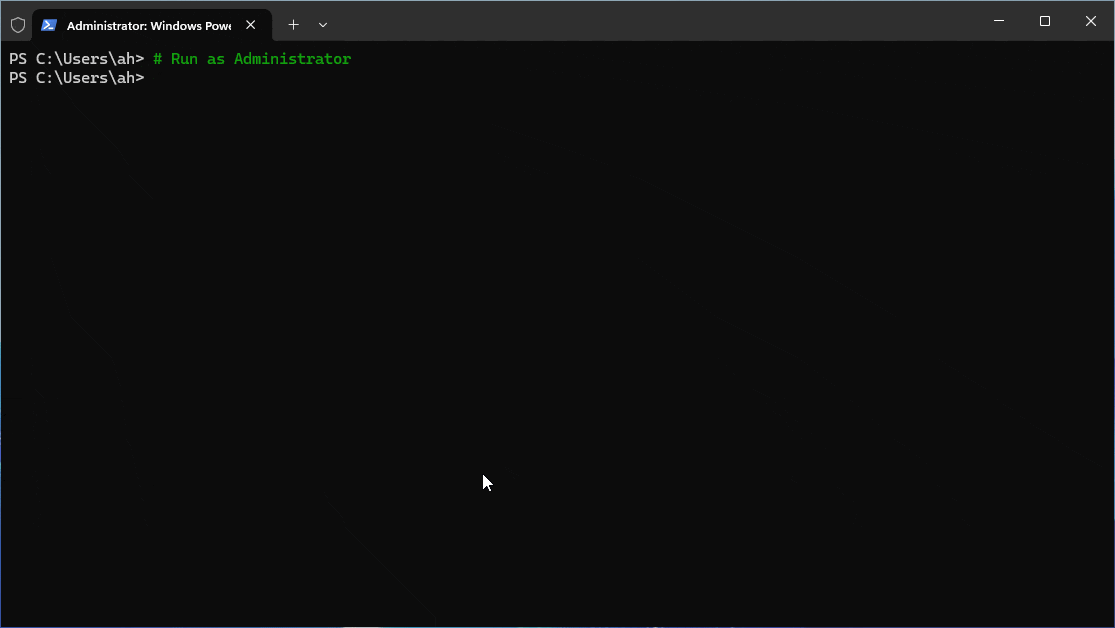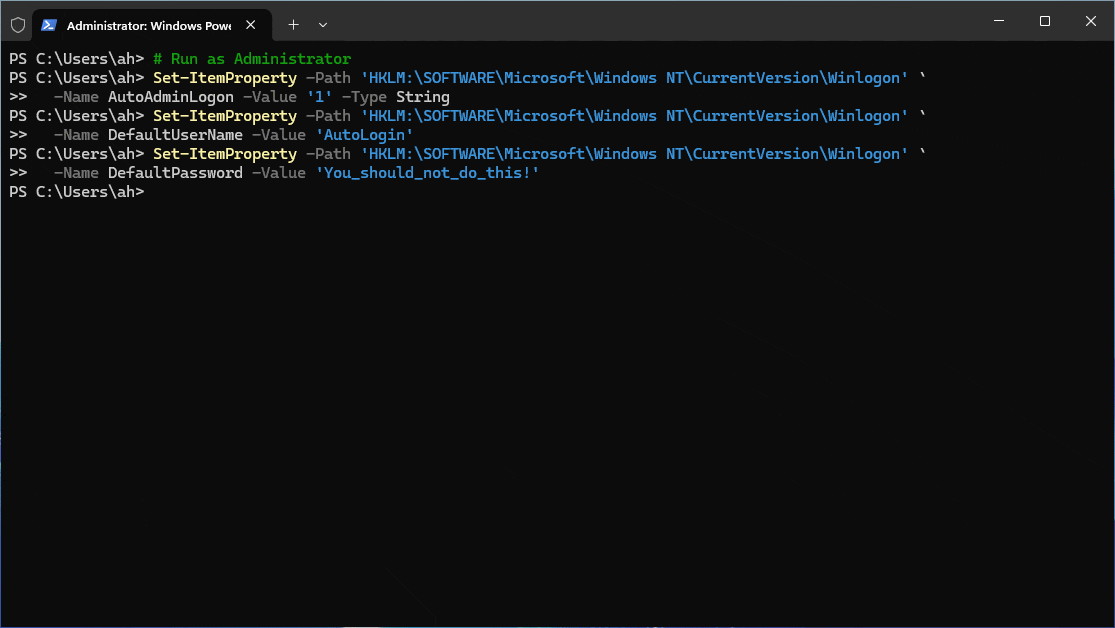
In case you wonder how to create the user in the first place, this is how to do it on a Windows Server 2025 and create a local user with no admin rights.

So why do you want not to do Windows Server 2025 Autologon? Everyone with the access rights to open the registry and read the Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon registry key, can read this in clear text.

Long story short, when you now reboot winlogon.exe fires, it reads those values and feeds them to msgina.dll, circumventing any user interaction.
Use Sysinternals Tool Autologon to Configure AutoAdminLogon
Autologon.exe by Mark Russinovich wraps the same registry flow but stuffs the password into an LSA secret. That at least requires admin privileges plus the Security privilege to retrieve it, raising the bar beyond simply using the registry editor.
Download the standalone binary or pull it with winget in one lazy line:
winget install --id Sysinternals.Autologon -e --silentIf you are not familiar with winget yet, please check my guide here and use my script here, to automatically install my daily used Sysinternals tools on your developer devices.
Now run autologon from a command line tool of your choice with admin rights and this is the configuration required. I am using the local user configured earlier.


The password will now be stored in the HKEY_LOCAL_MACHINE\SECURITY area. This area is normally not visible and i will not explain how to get access to this in my blog. It is still relatively simple to do for an experienced hacker, but it adds a layer of security.
Sysinternals Autologon sprinkles a thin layer of encryption over the registry trick – good enough for homelabs, but it is still not Fort Knox and not secure enough for production.
How to Secure Windows Server 2025 Autologon to the Maximum?
Think about adding security in layers here. Keep in mind, that I would still only ever consider this as the very last resort in a production environment and discuss all risk mitigation issues required with the highest level of IT Security and the product owner of the product requiring this.
- Only use local accounts
- Create a Least-privilege accounts and work hard in adding rights to the registry and fileserver to avoid admin rights at all costs
- Do not domain join the machine needed – unless this is a security requirement
- Run the machine as seperated as possible. Think about running this on it’s own Hyper-V or other virtualization solution with very limited access to, so no one can access it’s GUI or filesystem.
- Make sure the backup is as protected as the virtual machine
- Use technology like Credential Guard, LSA protection, Bitlocker and Windows Defender to increase the maximum level of security.
- Track any implementation as technical debt and seek mitigation
There are more modern technologies available to secure Windows Server 2025 Autologon, so you can mitigate and reduce risks.
Conclusion and recommendation
Avoid Windows Server 2025 Autologon at all costs. If you have to do it make sure you involve risk management and IT Security and implement as much risk mitigation tools and options as possible. I want to highlight again, that I highly discourage using this in production and even in a homelab, implement as many of the security measure mentioned above.
If you have any questions please don’t hesitate to reach out to me on LinkedIn, Bluesky or check my newly created Adaptive Cloud community on Reddit.
– LinkedIn
– Bluesky
– Adaptive Cloud community on Reddit





