Managing local administrator accounts securely is a critical aspect of maintaining a robust and secure IT environment. With the introduction of the Windows Local Administrator Password Solution (LAPS) in newer versions of Windows, Microsoft has provided a modernized tool to centralize and automate the management of local administrator passwords for Windows Clients and Server Operating Systems.
In this article, we will explore how to implement and use Windows LAPS as an addition to our HomeLab to secure your local administrator accounts, leveraging the latest features and best practices.
Table of Contents
What is Windows LAPS?
Windows LAPS is an evolution of the traditional Local Administrator Password Solution, now integrated directly into Windows Server and client operating systems. This solution allows you to manage local administrator accounts by storing their passwords in Active Directory (AD), ensuring they are secure, unique, and regularly rotated.
Requirements
Windows versions that support Windows LAPS:
- Windows 11 22H2 and later
- Windows 10 with the April 2023 update
- Windows Server 2025
- Windows Server 2022 with the April 2023 update
- Windows Server 2019 with the April 2023 update
Domain functional level requirements:
Your Active Directory domain needs to be 2016 Domain Functional Level (DFL), before you can enable Windows LAPS password encryption. There is a limitation with any Windows Server Domain Controller. Those don’t support Windows LAPS and therefore can’t use the DSRM account management feature.
More details are available here.
Setting Up Windows LAPS
Extend the Active Directory Schema
Ensure you have the necessary permissions to perform this action. Open an elevated PowerShell console and run the following command to update the schema:
Update-LapsADSchema
Configure Group Policy
To enable LAPS, you need to create and apply a Group Policy Object (GPO).
- Open the Group Policy Management console and create a new GPO or edit an existing one.
- Navigate to
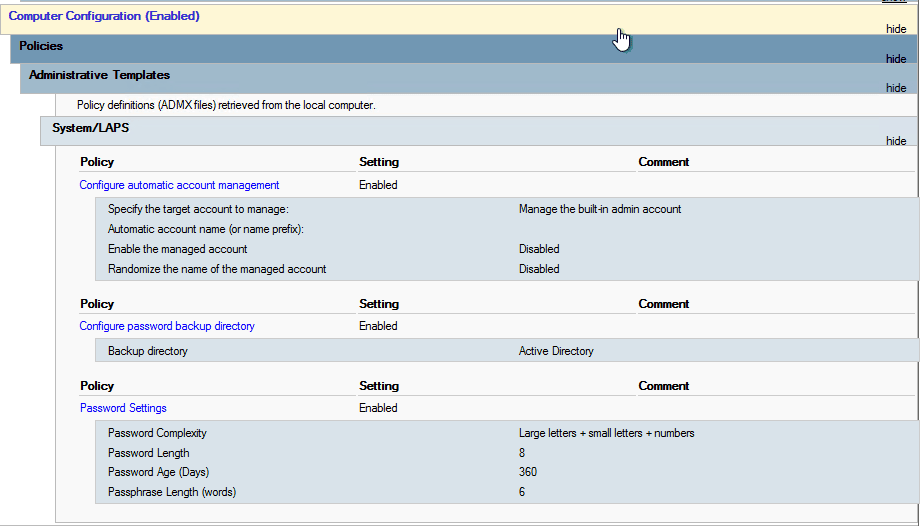
Computer Configuration>Policies>Administrative Templates> System >LAPS. More details here. - Enable the
Password Settingspolicy and configure the settings as needed, such as password length, complexity, and rotation period.
For security guidance please discuss that with your IT Security team and enable a mimum requirement for your personal “well being”. In my lab I keep things simple and only want to manage the local administrator password for demonstration and testing purposes.
Apply the GPO:
- Link the GPO to the appropriate Organizational Units (OUs) that contain the servers or clients you want to manage with LAPS.
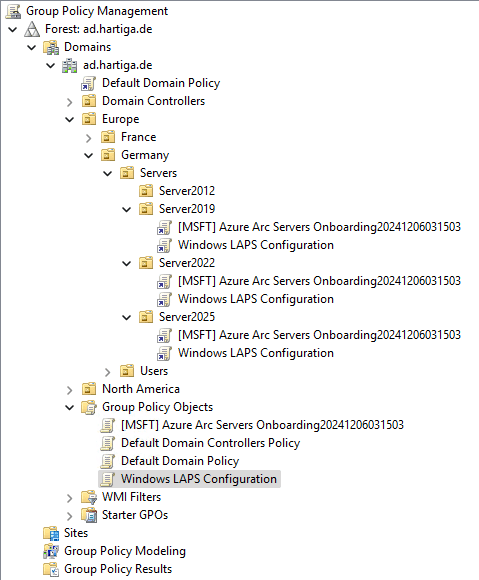
Grant Permissions
After linking the GPOs you need to enable the LAPS for managing these OUs, with the following command
Set-LapsADComputerSelfPermission -Identity "OU=Servers,OU=Germany,OU=Europe,DC=ad,DC=hartiga,DC=de"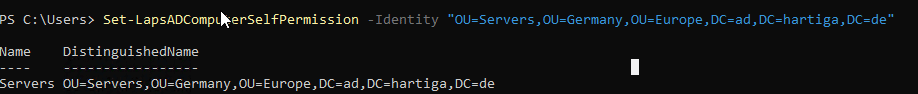
Important:
- If inheritance is enabled, running the command on a parent OU (e.g.,
OU=Servers,OU=Germany,OU=Europe,DC=ad,DC=hartiga,DC=de) will propagate the permissions to all nested OUs automatically. - If inheritance is disabled on any child OU, you will need to run the command separately for those specific OUs.
If you prefer to set the inheritable permissions on the root of the domain, this is possible by specifying the entire domain root using DN syntax. For example, specify ‘DC=hartiga,DC=de’ for the -Identity parameter.
Best Practice:
To ensure proper permission application:
- Verify that inheritance is enabled for all child OUs using tools like Active Directory Users and Computers (ADUC) or PowerShell.
- If inheritance is disabled on some OUs, manually run the
Set-LapsADComputerSelfPermissioncommand for each affected OU.
Verifying LAPS Configuration
Wait until a Group Policy Update occured on your servers enabled for Windows LAPS or run
gpupdate /forceYou can now verify and check for the LAPS password.
Get-LapsADPassword -Identity "file-2025" -AsPlainText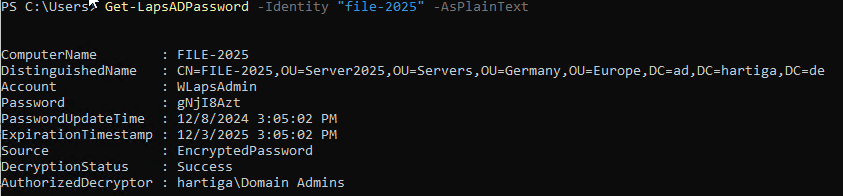
Configuring Windows LAPS on Teams Rooms on Windows
If you want to take Windows LAPS to the next level, i highly recommend to read this Microsoft Learn article: https://learn.microsoft.com/en-us/microsoftteams/rooms/laps-authentication?WT.mc_id=MVP_416291
Learn how Windows Local Administrator Password Solution (LAPS) helps you manage and backs up local administrator passwords for Teams Rooms on Windows devices using Entra ID and Intune.
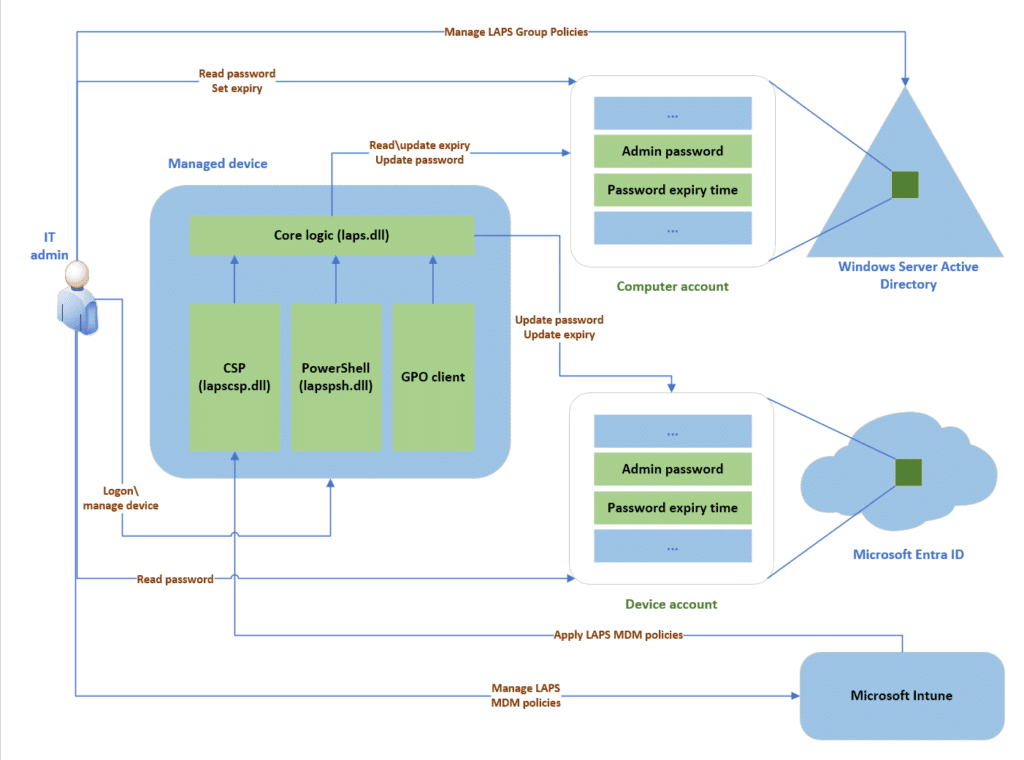
Conclusion
Windows LAPS is a powerful tool for securing local administrator accounts by centralizing password management and automating password rotation. By following the steps outlined above and ensuring proper configuration and permissions, you can significantly enhance the security of your IT environment.
In today’s security-conscious world, tools like Windows LAPS are essential for maintaining compliance and protecting against unauthorized access. By integrating LAPS into your security strategy, you can ensure that your local administrator accounts are well-protected and managed efficiently, reducing the risk of security breaches and improving overall network security.
IMPORTANT: This is a very basic article on Windows LAPS. If you want to enable it, please make sure that you involve all groups in your organization i.e. IT-Security, Server Teams, Helpdesk Teams and create a Role Base Access Control Design and carefully implement the settings across the OUs with Clients and Servers. If done incorrectly or with a lack of communication you might cause business impacts or security incidents. Use Test Systems.





